Application Authorization
Plug-and-play authorization for modern applications, no need to build from scratch.
Decoupling Policy from Applications for Granular Authorization
Modern applications built utilizing microservices have created an expanding cybersecurity challenge. The number of connections has grown by ten times or more, and the once-reliable gateway or firewall security checkpoint in front of a monolithic application no longer suffices.
Also, application developers building authorization for customer-facing cloud native applications, and IAM teams working to bring entitlements into a cloud native era require a physically distributed but logically centralized authorization system.
Policy as Code For Modern Applications
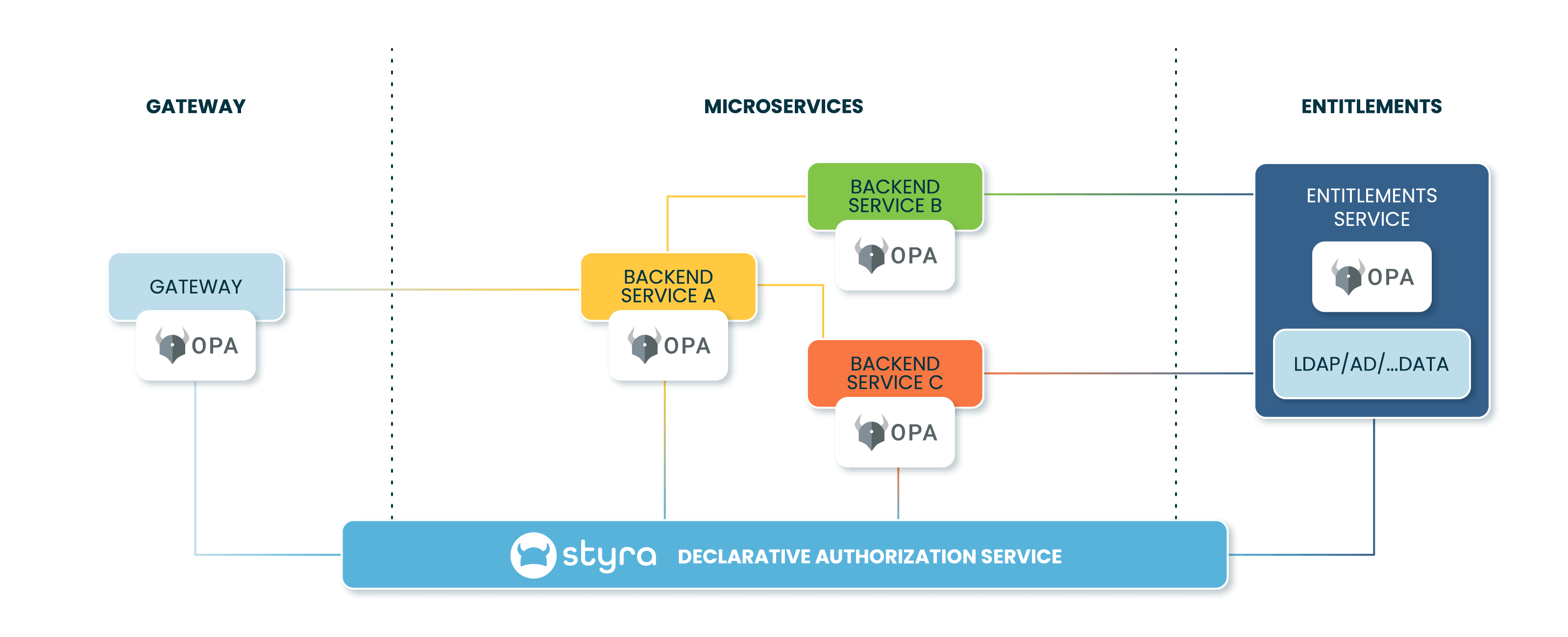
Benefits Across the Stack
Secure Your Stack Once
Use policy as code to separate permissions from your technology choices to keep your teams on the leading edge without impacting security.
Remove Latency
Bring authorization decisions closer to enforcement points, and accelerate the migration of applications to the cloud.
Work Across Clouds and Containers
Standardize on authorization just like monitoring, logging, and deployment.
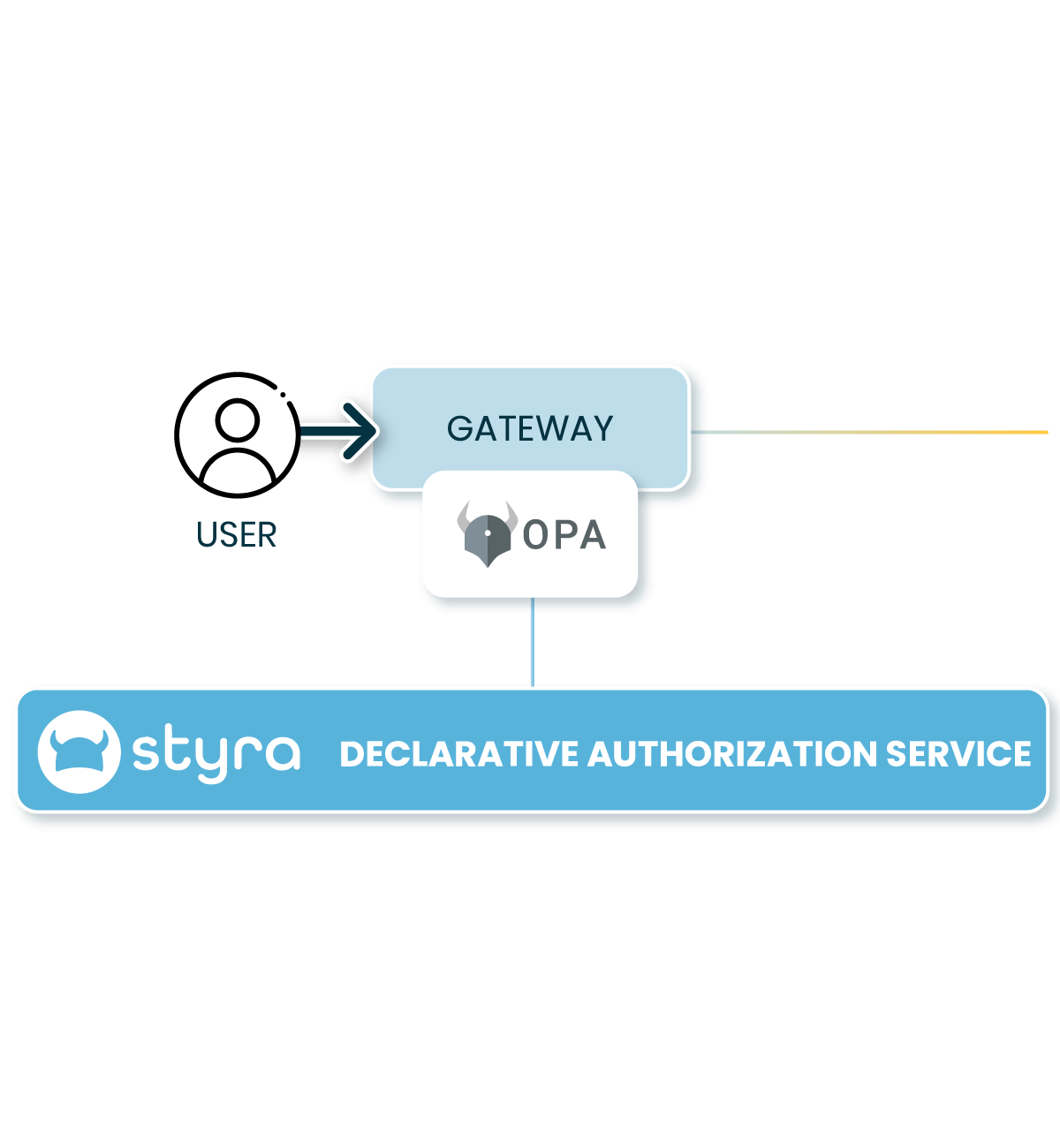
Policy Enforcement at the Gateway
Easily enforce security policies over client API requests for microservices while keeping performance and scalability intact.
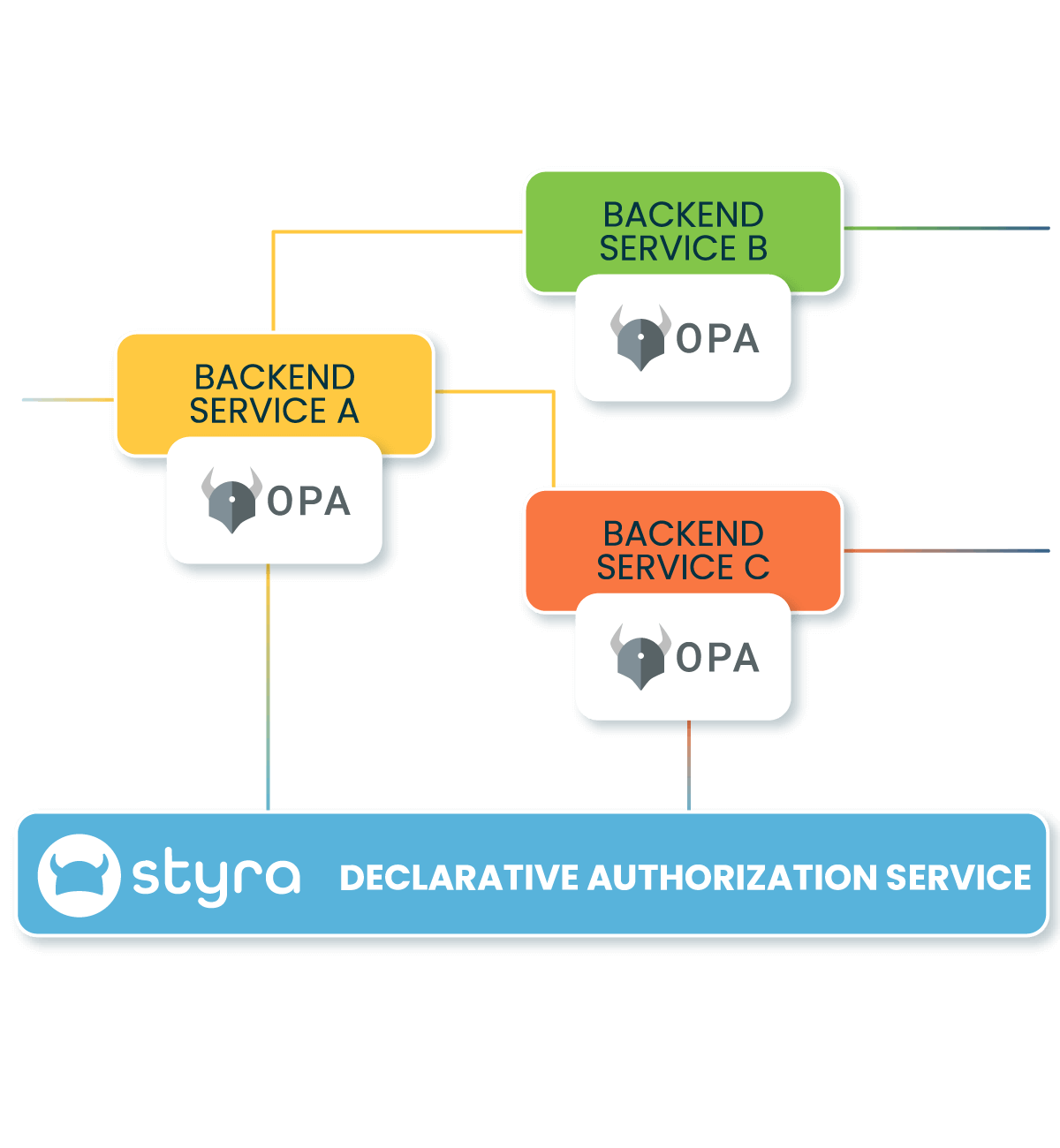
Control Communication Between Microservices
Decouple authorization policy and decisions to secure users, APIs, and service meshes. Limit lateral movement and reduce the risk inherent in microservices without increased latency.
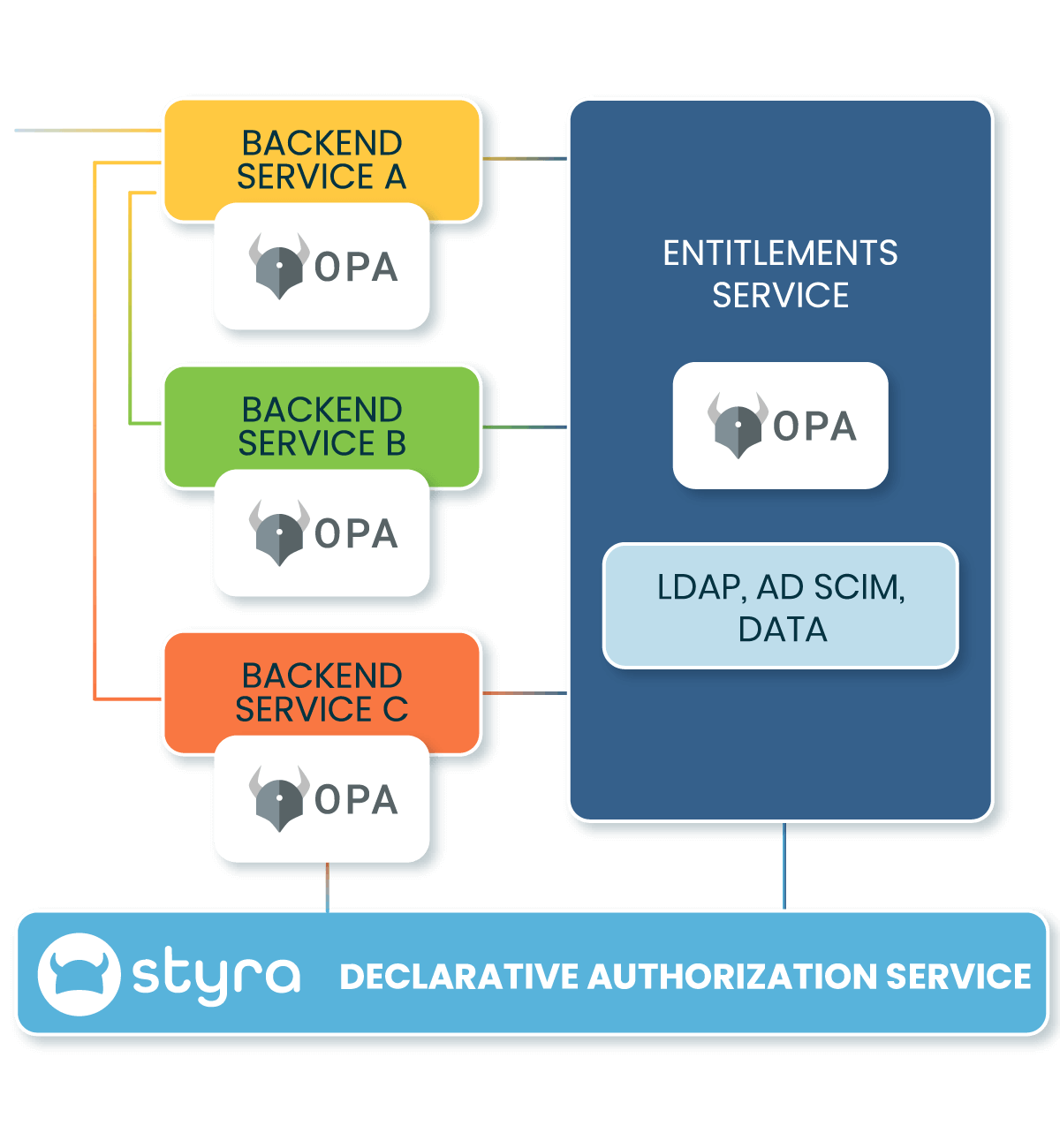
Migrate Apps with
Cloud native Entitlements
Quickly and easily make existing entitlements data sources, including LDAP, AD, and SCIM accessible for applications migrated to the cloud.
Cloud native
Authorization
Entitlement Explosion Repair
Join Styra and PACLabs on April 11 for a webinar exploring how organizations are using Policy as Code for smarter Access Control.
Speak with an Engineer
Request time with our team to talk about how you can modernize your access management.