OPA Management: Challenges and Opportunities
The Open Policy Agent (OPA) is a policy engine that brings the speed, reliability and flexibility of decoupled policy as code to a wide range of authorization use cases across the cloud-native ecosystem.
OPA is a Cloud Native Computing Foundation (CNCF) graduated project and has become an industry-wide standard for authorization, with several leading enterprises implementing it in their business-critical cloud systems. However, deploying OPA at scale can present some challenges, especially regarding administration and management.
In this article, we talk about a few of the challenges of OPA management and how you can solve them using Styra Declarative Authorization Service (DAS). Styra DAS is a turnkey management plane for OPA that saves you the time and effort of designing one on your own.
The importance of OPA
Open Policy Agent is an open-source general-purpose policy engine designed specifically for the cloud-native environment. It allows you to decouple policy from the underlying application code using a high-level declarative language called Rego. As a policy decision engine, OPA receives query input from the application and judges it against the policy and data provided. Upon reaching a decision, it returns a JSON value to the application.
The decoupling of policy lets you update or change policies without having any impact on other functions of an application. The policy code also becomes reusable across the entire application. In a microservice application with thousands of components, you can integrate OPA alongside each service as a sidecar, leading to unlimited scaling.
OPA also unifies policy as code across the entire organization. Unified policy as code means using a single policy framework and the same policy language across multiple applications and infrastructures. This unification allows anyone in the organization to handle policies, making communication and collaboration between security, compliance and developer teams straightforward.
As Styra discovered in our 2022 Cloud-Native Alignment Report, 97% of IT decision-makers are planning on expanding their usage of cloud-native tools and technologies. Being general purpose and domain-agnostic means that OPA works for various use cases across the cloud-native stack.
Read the Starter’s Guide to OPA to learn more about the basics of cloud-native authorization and the importance of policy as code in application and infrastructure security.
Challenges in Open Policy Agent management
OPA was initially designed to solve the authorization problems of a single developer, not an entire organization. While OPA is still an ideal tool for policy decision-making, it has the following shortcomings when it comes to enterprise-grade implementation:
— OPA is designed for central management. It exposes management APIs, but designing and maintaining your custom central control plane can be time and resource intensive.
— OPA does not come with a central system to distribute and manage policies over the entire cloud-native stack, especially across multiple applications and infrastructures. Without a central management plane, teams can have difficulty figuring out what parts of the environment are affected by their policies.
— Even after integration with an application, OPA needs to be loaded with policies and data to make authorization decisions. To use a Git repository to store and maintain policy code, developers need a way to fetch the policy bundles and distribute them to the right OPA deployments.
— Not every developer will have mastered the Rego policy language. Without a policy library, it is manually intensive to translate a JSON schema into Rego to test it in OPA. Teams who don’t have a shareable policy library may see reduced overall deployment speed and overburdened OPA experts.
— OPA does not provide a monitoring environment to catch or fix policy violations. Users need to find a way to test and validate policies before deploying them. OPA alone does not provide a way to check a new policy against historical OPA decisions.
— Not having built-in decision logging and reporting features makes it challenging to communicate the effectiveness of policy as code systems to other stakeholders, especially non-coders.
Enterprise-ready OPA management with Styra DAS
To address these challenges, Styra — the creators of OPA — built Styra DAS, the industry’s first control plane for OPA.
As companies began rolling out OPA into production, we recognized their need to meet security and compliance requirements at scale. According to a report by Cybersecurity Insiders, 72% of companies placed security above all else when designing an Identity and Access Management (IAM) solution.
Some very large enterprises that adopted OPA early on, such as Netflix and Pinterest, designed their custom control planes for OPA management. However, not everyone has the time or the resources to build a bespoke solution, leading to the build vs buy dilemma.
Styra DAS for OPA enables developers to focus on the business logic of application development and make better, more secure apps instead of being burdened with designing an authorization solution. Here are some of the features it comes with:
— Pre-built policies: Styra DAS has a built-in library of more than a hundred Kubernetes policies, including policies for K8s Admission Controller. It also includes policy packs for best practices, PCI, MITRE ATT&CK for the cloud and CIS benchmarks to meet Kubernetes compliance regulations. Developers can quickly make prototypes for sample apps and data load multiple policy enforcement points.
— Shareable policy libraries: Custom policy libraries can be shared across teams and clusters to increase deployment speed and reduce the burden on Rego experts. This sharing can also minimize human error and central policy as code can improve security and compliance.
— 9+ built-in integrations: Since OPA is a general-purpose policy engine, its list of integrations is constantly increasing. Styra DAS supports the most popular integrations out-of-the-box, such as Kubernetes, microservices and cloud configuration. You can simply download an integration through Styra DAS and automatically add it to your OPA deployments.
— Auditing and monitoring functionality: Styra DAS can store and archive decision logs and allows you to inspect Git configurations, providing an easy method of auditing policy changes. The DAS graphical user interface (GUI) includes a dashboard for data visualization, which enables you to monitor policies in real-time and respond quickly to high-risk violations.
— Validation: Using the Decision Replay function, you can compare policies against historical decision logs to see their impact before implementing them.
— Policy authoring: Styra DAS provides a GUI instead of a text editor for authoring policy. Built-in rules and compliance packs, along with decision logs showing the input and output of policy decisions, let staff members with no knowledge of Rego select policies they need and see their impact before making any changes.
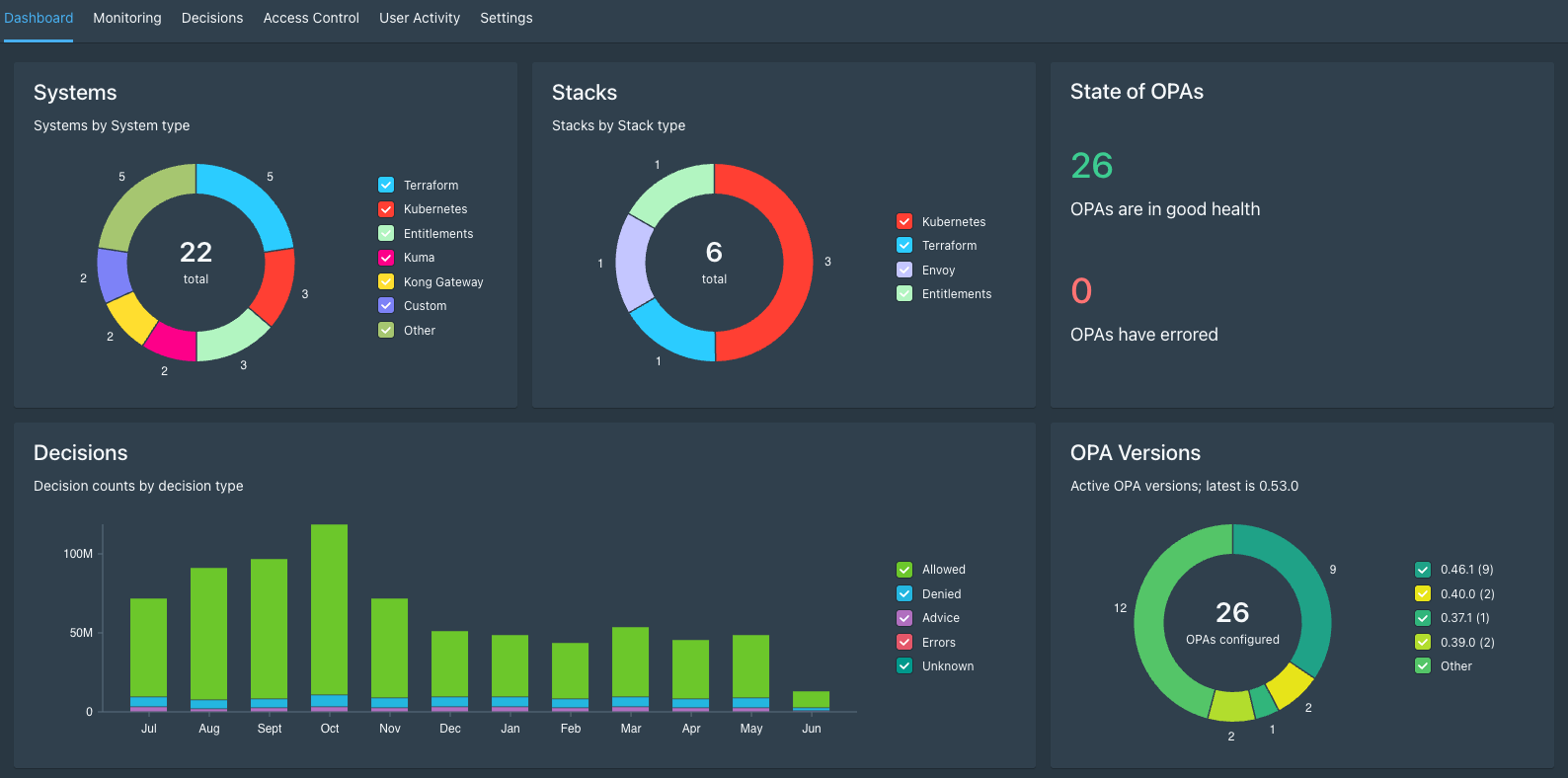
Visualize and monitor compliance violations in real-time with the Styra DAS dashboard.
Styra DAS is available in two versions to let teams of any size and budget operationalize OPA. Both versions have complete access to the full suite of Styra DAS features.
— Styra DAS Free can help you get started with the adoption process. It supports up to four systems and integrates with two team members and a single external data source.
— Styra DAS Enterprise has unlimited scope, scalability and round-the-clock support.
FAQs
How can I learn more about OPA policy authoring?
You can enroll in free courses at Styra Academy to start learning Rego and writing policies for OPA. The Rego Playground lets you test and share policies if you’re a more advanced user.
What are the benefits of infrastructure-as-code?
Infrastructure-as-code allows faster infrastructure configuration and leads to a more stable and scalable environment. Automated processes also reduce human error.