Policy Guardrails for Kubernetes
Enforce best practices using policy as code guardrails at Kubernetes Admission Control across all Kubernetes clusters.
Secure Your Clusters with Policy as Code
Kubernetes is the industry standard for cloud-native container orchestration, and as such, pod and cluster security has become a critical component of any security strategy and architecture.
See how Styra helps DevOps and platform teams enforce security and compliance best practices by default, manage PodSecurityPolicy (PSP) deprecation and systematically reduce Kubernetes production risk across countless clusters in complex enterprise environments.
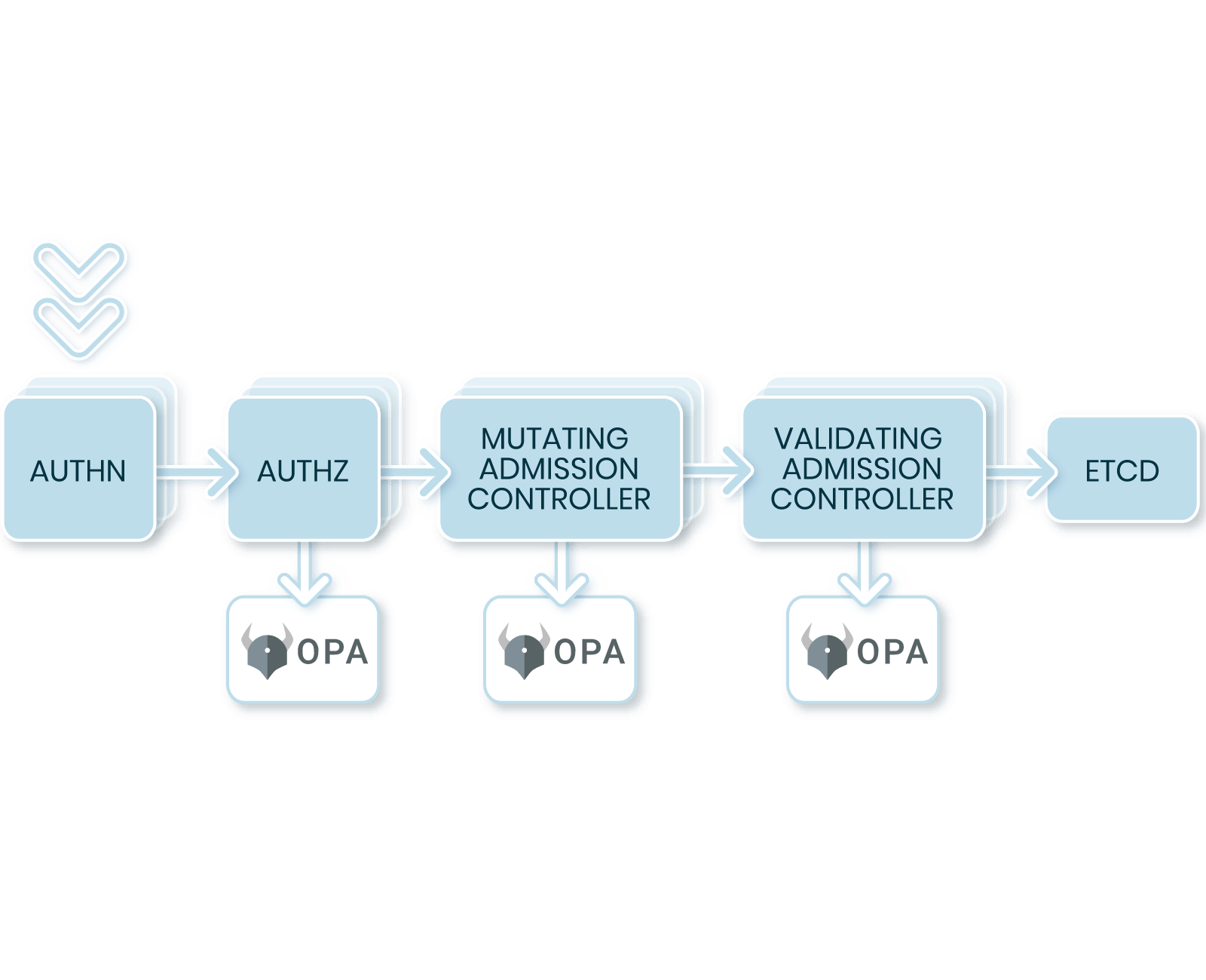
Transform K8s Security
Deploying Kubernetes across AWS, Azure, GCP and self-hosted environments teams can now easily enforce security and compliance best practices using policy-as-code guardrails at Kubernetes Admission Control. With an industry-leading authorization toolset, teams can eliminate manual policy creation, validate policy changes before impact, monitor all non-compliant resources, easily audit decisions. Get started and instantly enforce best practices with pre-built Compliance Packs for NIST SP 800-190 Application Container Security, Pod Security and more.
Deliver Secure Streamlined
Kubernetes Deployments
Secure the Business
- Systematically reduce production risk across clusters
- Prevent misconfigurations, production outages and security incidents with fine-grained access control (FGAC)
- Reduce unwanted cloud costs with resource limits
- Align policy-as-code strategy across business, security and compliance teams
Reduce Manual Efforts
- Eliminate manual policy creation and maintenance with validated libraries and easy-to-use policy templates and editing tools
- Eliminate DIY engineering investments with an out-of-the-box authorization toolset
Scale Policy as Code
- Instantly deploy a mature policy-as-code strategy on Kubernetes
- Start anywhere and scale to thousands of clusters
- Grow with the guidance and support of the creators and maintainers of Open Policy Agent
Leverage Kubernetes Compliance Packs
Make compliance simple with pre-built compliance policy packs for the standards that matter, including:
- NIST SP 800-190
- PCI DSS
- MITRE ATT&CK
- CIS Benchmarks
- Pod Security
From Open Source, a Path to Scale
The outstanding OPA developer community has built open-source tools that work well for many Kubernetes deployments. At enterprise scale, these tools can require extensive DIY engineering investments and constant maintenance to meet the requirements of mature organizations. Teams should bear in mind that policy as code typically extends beyond Kubernetes, as enterprises adopt broader security and compliance authorization initiatives across infrastructure and applications — requiring a single, extensible approach to policy as code.
From Day 0 to Day 2, scale with a fully mature enterprise Kubernetes feature set, including:
- Multi-cluster policy management (tens to thousands of clusters)
- Multi-cloud support
- Impact analysis
- Shift-left for CI/CD authorization
- Context-aware, data-driven policy
- Compliance view for all non-compliant resources
- Custom snippets matching Gatekeeper CRD functionality
- Auditing
- Policy libraries and compliance packs
- OPA Gatekeeper to Styra migration path
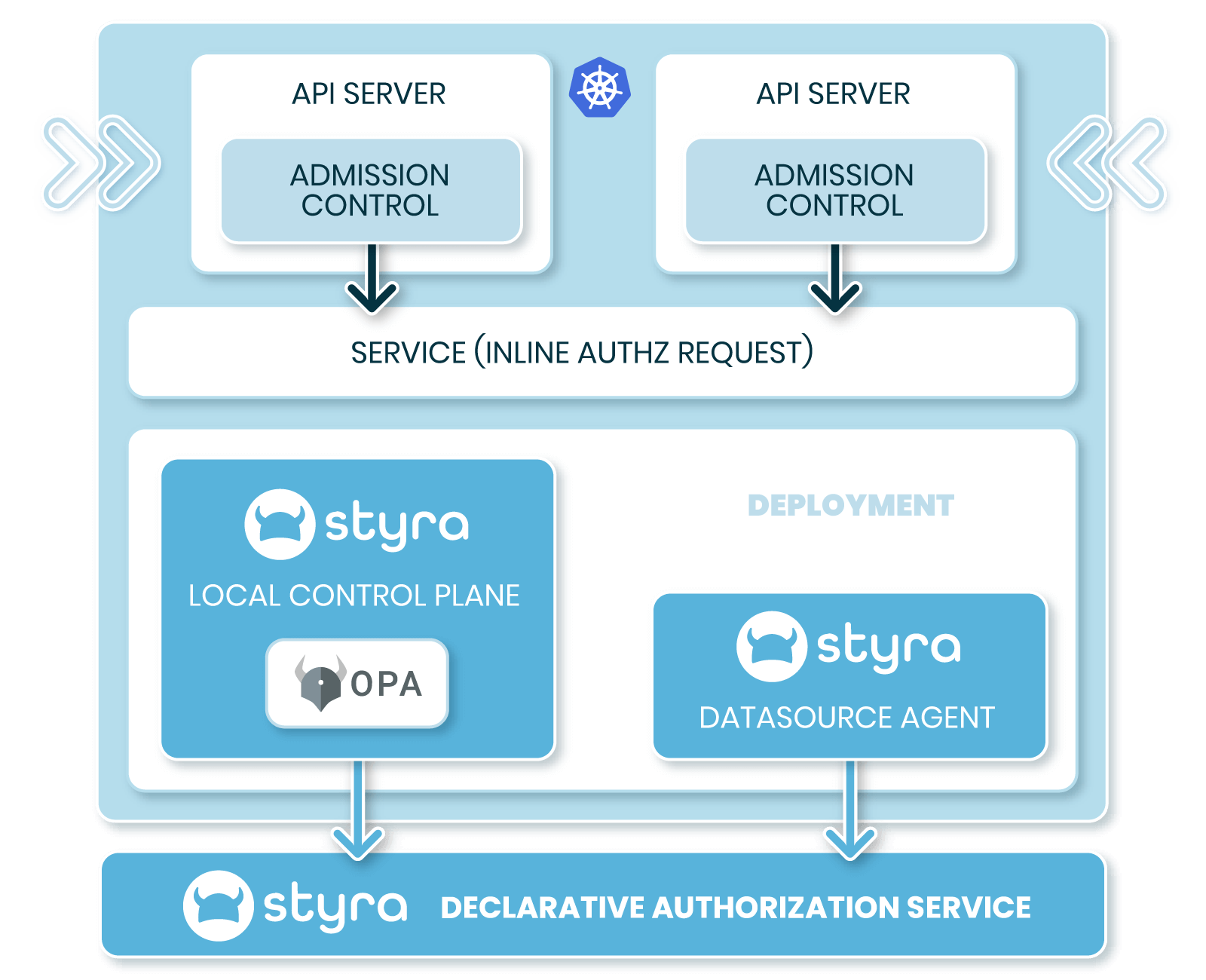
Manage OPA for Kubernetes
Manage policy as code at scale — across large, complex Kubernetes deployments with tens to thousands of clusters, in highly regulated environments and extend policy as code across Terraform, and CloudFormation as needed.
Styra DAS + Kubernetes Hands-On Workshop
See how Styra DAS automatically implements and enforces policy guardrails for your Kubernetes clusters. The lessons learned will help you shift security left using a declarative model that works with Kubernetes admission control.
Cloud native
Authorization
Entitlement Explosion Repair
Join Styra and PACLabs on April 11 for a webinar exploring how organizations are using Policy as Code for smarter Access Control.
Speak with an Engineer
Request time with our team to talk about how you can modernize your access management.