Secure Your Gateways
Enforce authorization at the API Gateway level.
Enforce Policy at the API Gateway Level
It wasn’t too long ago that coarse-grained access control lists (ACL) rules on a network firewall were enough to satisfy security requirements. As application architectures have become more distributed — composed of multiple microservices, housed in containers — the way we control access between resources has evolved from focusing on hosts/IPs to one based on services and message payloads.
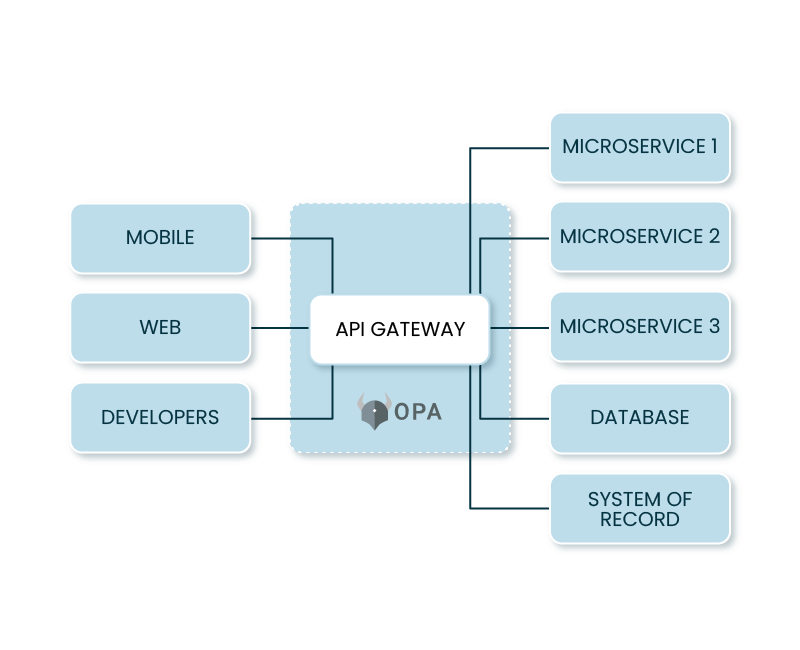
Unify Policy Lifecycle Management for Ops and Devs
- Manage policy lifecycle from authoring to monitoring
- Validate the impact of policy changes before deploying
- Distribute policy across clusters, clouds and teams
- Monitor authorization decisions in real-time and in logs
- Rapidly implement leading open-source solutions at enterprise scale, such as Kong and Envoy
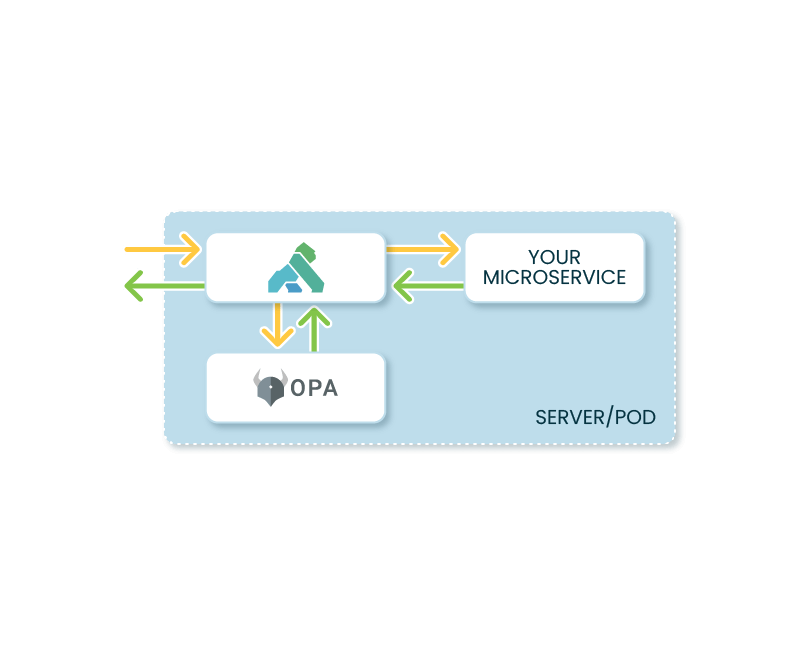
Extend Enterprise-grade Lifecycle Management Across Kong Mesh
- Automate policy-as-code for your service mesh
- Provide visibility to monitor and audit traffic flow and decisions in real-time
- Increase application reliability with policy-based traffic management

Command Some of the World’s Most Powerful API Gateways
Use Rego to command the top API gateways, including Kong and Emissary.
FAQ
What is an API Gateway?
An API gateway is a tool used to increase security, scalability and efficiency of APIs and backend microservices by providing them a single entry point. They expose the API endpoints, which are accessible by the public, push incoming requests to the desired services, transform them as needed, and package the data in the response before sending it back to the front-end client. In acting as a single entry point for a system, API gateways restrict access to microservices from outside entrants, reducing attacks.
Why do teams need authorization at the service mesh gateway?
Using API gateways ensures that only valid requests, recognized by the gateway, are allowed through, as well as being significantly easier and more efficient than implementing that logic in each and every service, which would mean replicating the access logic in several different locations. By using API gateways, that access logic all coalesces into one place, making it safer and more efficient not only to defend the system, but also to deploy new software and changes for existing applications.
What is an example of microservices authorization policy?
Policy-as-code can be used to enforce all sorts of controls upon a system, from complex rules with several prerequisites to authorization, to rules as simple as allowing a single user. For example, a policy may state that a specific user, let’s call him Bob, may access a certain resource as it does not pertain to his job. Such a rule could be expressed through code and enforced across a system, barring Bob access to that resource.
Cloud native
Authorization
Entitlement Explosion Repair
Join Styra and PACLabs on April 11 for a webinar exploring how organizations are using Policy as Code for smarter Access Control.
Speak with an Engineer
Request time with our team to talk about how you can modernize your access management.